
That’s not our admin: The blind spots that open doors to attackers
Lessons from around 600,000 security alerts analyzed by Barracuda Managed XDR
Takeaways
- In 2025, 90% of ransomware incidents exploited firewalls, and the fastest observed ransomware case took three hours from breach to encryption.
- The most widely detected CVE vulnerability dates from 2013, and 11% of detected vulnerabilities have a known exploit.
- Barracuda releases the Managed XDR Global Threat Report.
Cyberattacks are stealthy. They sneak into networks, looking for gaps, errors and oversights: a single rogue device, an account that wasn’t disabled when someone left, a dormant application that hasn’t been updated, or an accidentally disabled security feature. They’ll try to trick employees and steal their identities, take advantage of legitimate IT tools and join privileged access groups. Much of this will look like everyday IT activity.
For organizations and their security teams — especially if that ‘team’ is a single IT professional — this presents immense security challenges. With limited resources and visibility and a stack of fragmented security tools, they must safeguard identities, assets and data from attacks that can unfold in a matter of hours or lurk in the network for months.
How attackers target organizations and the security gaps that increase risk
The new Barracuda Managed XDR Global Threat Report highlights the tactics used by attackers over the last 12 months — and the security gaps exposing organizations to risk.
The threats are real, not theoretical. They are drawn from a unique, real-world dataset of more than two trillion IT events collected during 2025, around 600,000 security alerts and roughly 300,000 protected endpoints, firewalls, servers, cloud assets, and more. The data is complemented by incident summaries and practical steps on how to stay safe and cyber resilient.
The purpose of the report is to help IT and security professionals in resource-constrained organizations better understand how attackers target potential victims and the security weak spots they try to exploit.
Who’s really logging in, using that tool, joining that group?
The findings show how attackers exploit legitimate IT tools such as remote access software and leverage unprotected or rogue devices. They also highlight the risks of outdated encryption, disabled endpoint security, and more, and the warning bells of unusual login or privileged access behaviors.
Key findings
- 90% of ransomware incidents exploited firewalls through a CVE (a classified software vulnerability) or vulnerable account. Attackers can use this to gain access and control over the network and bypass its protection, hiding malicious traffic and activity.
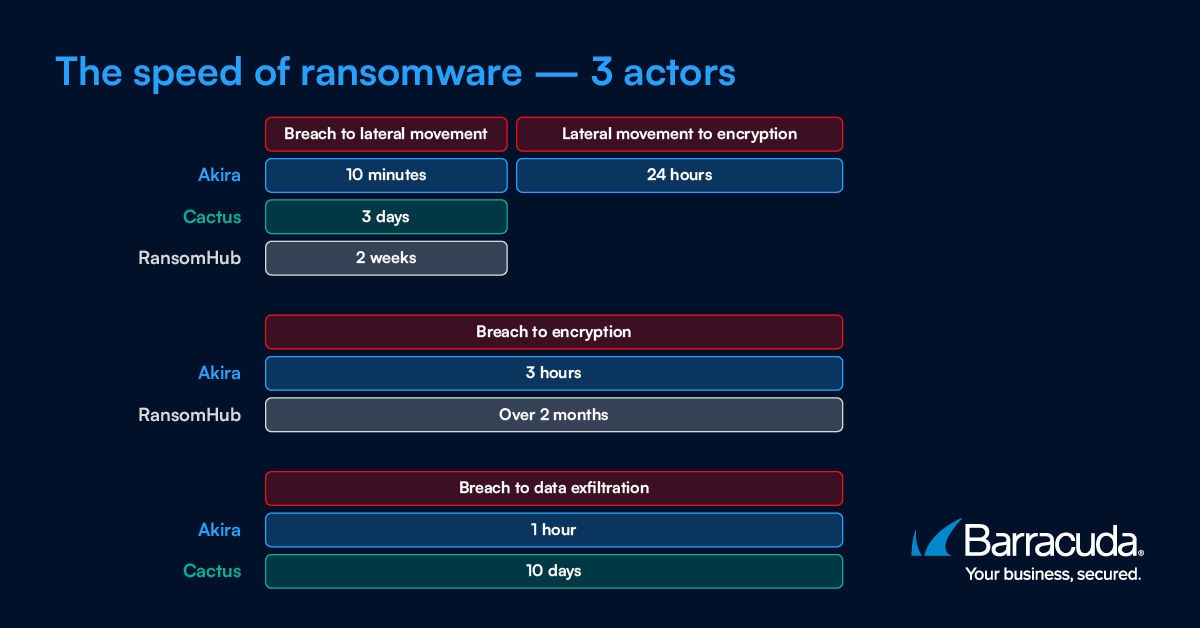
- The fastest ransomware case observed involved Akira ransomware and took just three hours from breach to encryption. Such compressed timelines can leave defenders with minimal opportunity to detect and respond.
- One in 10 detected vulnerabilities had a known exploit. Attackers are actively weaponizing software bugs, often in the supply chain — and the importance of identifying and addressing unpatched software cannot be overstated.
- The most widely detected vulnerability dates to 2013. CVE-2013-2566 is a flaw in an outdated encryption algorithm that can be found in legacy systems such as old servers or embedded devices or applications.
- 96% of incidents involving lateral movement ended with the release of ransomware. Lateral movement is the moment attackers lurking on an unprotected endpoint break cover, and it represents the biggest red flag of an unfolding ransomware attack.
- 66% of incidents involved the supply chain or a third party (up from 45% in 2024) as attackers exploit weaknesses in third-party software to breach defenses and extend their reach.
Expect the unexpected
The report shows that there is no ‘one-size-fits-all' when it comes to cyberattacks. Attackers are opportunistic and ‘kill chains’ are rarely, if ever, linear and neat.
Ransomware attacks are an excellent example. According to Barracuda Managed XDR’s detection and incident data, the fastest ransomware attacks in 2025 took just hours end-to-end, while the longest took months. Lengthy intrusions allow for maximum damage, and incidents that move at lightning speed can be harder to catch and contain before they’ve been executed.
Integrated protection
If left unresolved, a single red flag can quickly escalate into a widespread incident that disrupts operations, reduces productivity, compromises sensitive data, and damages financial stability and brand reputation.
Organizations need a unified security strategy that integrates advanced, AI-powered detection technologies with a fully autonomous SOC, complemented by user education, automated threat response and a resilient security culture.
Quick wins to strengthen protection are described throughout the report. They include consistent multifactor authentication and access controls, a robust approach to patch management and data protection, and regular cybersecurity awareness training for employees.
This should be underpinned by a comprehensive, managed security platform and 24/7 managed XDR solution that integrates network, endpoint, server, cloud, and email security — providing full end-to-end visibility and management control supported by a fully autonomous SOC.
For additional findings and insight, read the report here.

O Relatório de Invasão de Segurança de E-mail de 2025
Principais conclusões sobre a experiência e o impacto das violações de segurança de e-mail em organizações em todo o mundo
Subscreva o Blogue Barracuda.
Inscreva-se para receber destaques sobre ameaças, comentários do setor e muito mais.

Relatório de Insights do Cliente MSP 2025
Uma visão global sobre o que as organizações precisam e desejam dos seus provedores de serviços geridos de cibersegurança





