
Max Messenger: A fake data breach with genuine consequences?
Exploring the real-world fallout from a fabricated security breach
Takeaways
- The Max Messenger breach was initially reported as a major cyberattack but the hacker later retracted the claim, illustrating the real-world consequences of false attacks.
- Max Messenger, developed by VK for the Russian market, aims to replace popular messaging apps like WhatsApp and Telegram, which are being blocked by the government.
- Transitioning to state-backed messaging apps raises privacy issues, as personal data may be shared with the Russian government and exposes users to potential security risks.
- The incident highlights how misinformation and fake cyberattacks can undermine trust and have significant fallout, even when no actual breach occurs.
When you build a state-backed replacement for a popular messaging service, you may be putting your citizens’ information at risk. That’s the lesson that Russian officials may be taking from the recent Max Messenger breach — or at least, that’s the lesson that they would be taking had the hacker not retracted the claim.
What’s Max Messenger, and why is it important?
Max Messenger (“Max”) is supposed to be an “everything app” domestically produced by a Russian software company, VK. The software is supposed to combine payments, text chat and voice calls within a single application, broadly replacing the functionality of competing applications such as WhatsApp and Telegram. These apps are being blocked in Russia due to official concerns about their potential for fraud and terrorism.
Detractors point out that transitioning Russian citizens from foreign-owned applications to domestically produced software limits their freedom of choice. This move also places personal data in the hands of a notoriously oppressive regime. In addition, applications that are designed to be spied on are famously prone to security risks.
Misinformation undermines an intrusive application
Independent research suggests that Max shares everything from contact lists to geolocation data with parent company VK. What’s more, the app’s terms of service clearly state that this information can be shared with the Russian government.
As far as the Russian government is concerned, Max is mandatory. Since September 1, 2025, every electronic device in Russia must come with Max pre-installed. In addition, the government is starting to force public-sector education, housing and local government agencies to use the application.
In mid-January 2026, an attacker known as CameliaBtw claimed to have substantially breached the Russian messaging service. In addition to over 15 million complete user records, the attacker also claimed to have retrieved password hashes, communication metadata, infrastructure assets, and source code.
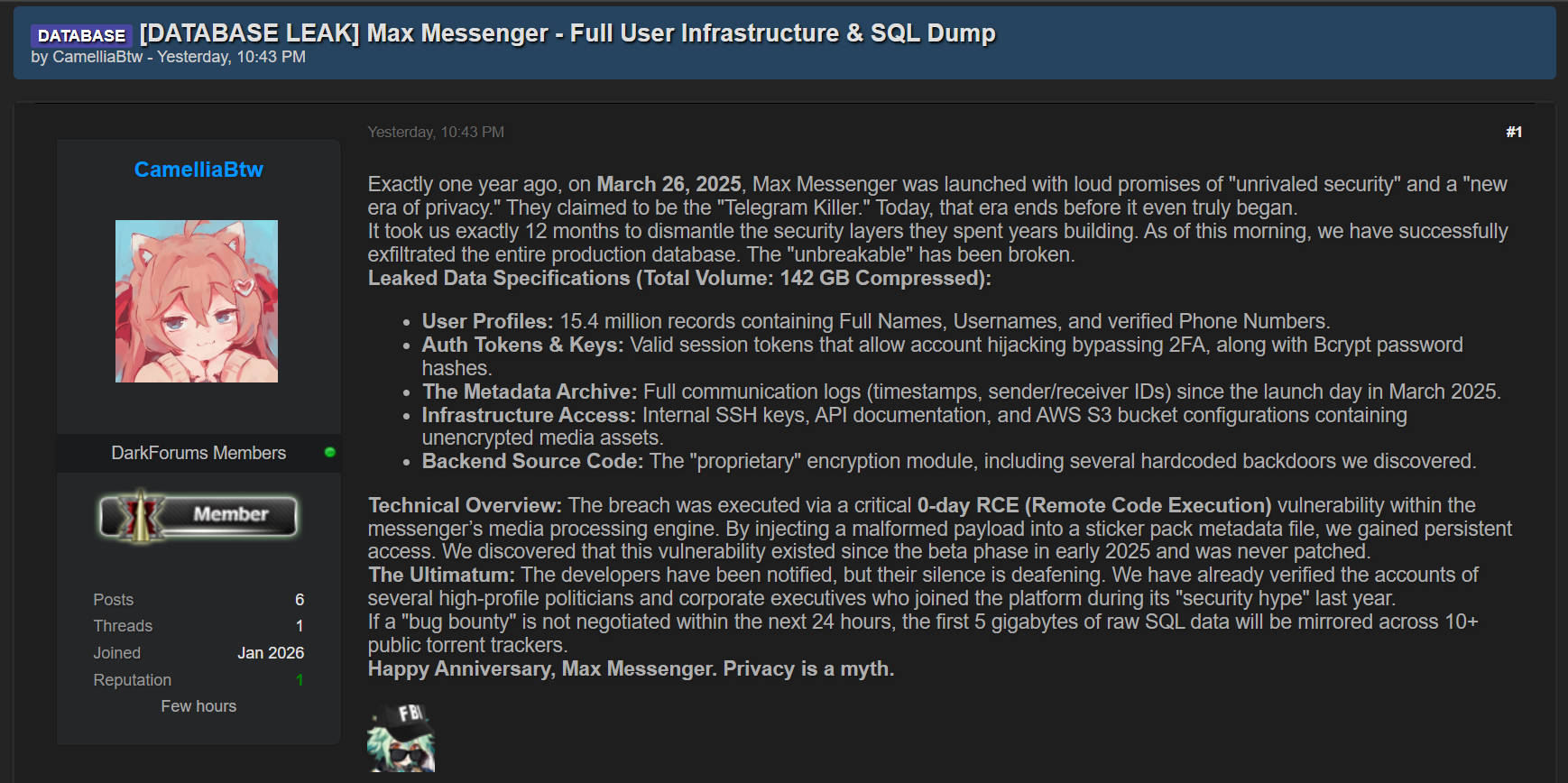
CamelliaBtw’s post on DarkForums (Image credit: Hackread.com
This would have been an enormously consequential breach — if it was real. Shortly after claiming to have breached Max, the same user clarified that they had never achieved a large-scale breach or uncovered any critical vulnerabilities.
Fake cyberattacks can be as damaging as the genuine article
Perhaps unsurprisingly, there is a history of false claims regarding major data breaches. For example, a Russian hacking group named Mogilevich claimed in 2024 to have penetrated servers belonging to Epic Games, exfiltrating 200 GB of data. The attackers quickly turned around and admitted that their breach was a ruse designed to raise their profile, but the damage had been done. Many users believed the attackers’ claim on its face and either missed or ignored their retraction, causing significant reputational damage to their intended target.
Similarly in 2024, the car rental giant EuroCar reported that convincing reports of a widespread data breach were likely generated by ChatGPT. The attackers’ assertion convinced many customers, though, because they even went to the trouble of creating fake records and email addresses. Even if no data breach actually occurs, attackers can still benefit by creating false claims of a data breach at someone else’s expense.
False hacking claims may affect Max Messenger adoption
As it stands, Russian internet users already somewhat distrust Max. The application is widely perceived to be buggy and insecure, with more utility as a tool of state repression than as a genuine “super-app.” Even the Russian Federal Security Service (FSB) initially blocked Max’s integration with other government services, citing the need for more robust encryption.
And although the government is intensely pressuring Russian citizens to adopt the Max app, there’s a difference between having the Max app on your device and using it every day. Here’s a likely failure of any mandatory government app: Citizens install the application as a show of compliance but continue to use other applications that are more convenient and less intrusive.
Meanwhile, there are many stakeholders who would be very interested in seeing this failure come to pass. The owners of Telegram and WhatsApp, for example — plus both NATO and the Ukrainian government — would all be happy to see the Max experiment fail.
Can we say definitively that the misinformation spread by CameliaBtw was a deliberate attempt by an interested party to derail adoption of Max in Russia? Absolutely not. Can we say that Russian citizens are already skeptical of Max and that they are primed to believe any damaging rumors about its security, regardless of their veracity? Absolutely yes.
Lastly, will we be surprised if there are more data breach claims about Max Messenger in the future, true or otherwise?
Is your application vulnerable to information security misinformation?
If you’re reading this, you’re probably not developing an intrusive super app on behalf of a repressive government (we hope). But you may also be wondering, “If an attacker falsely claims to have breached my critical systems, how do I prevent this falsehood from damaging my reputation and my business?”
Here are three suggestions:
- Make sure that you already have a good reputation
If you haven’t already been breached, try to bolster your security such that you’re a difficult target for attackers. Experiencing a data breach in the past means that consumers won’t have difficulty believing false claims in the future. - If you experience a data breach, be open
Make sure that your data breach response protocols are well-honed. If you do experience a data breach, this means that you can respond quickly and transparently, preserving customer trust. Even if someone spreads a rumor later on, customers will be more open to your refutation of it. - Invest in digital forensics
If someone falsely claims that you’ve been breached, you want to be able to respond with a quick and decisive “no.” Many attackers get away so cleanly that their breach announcement is the first indicator of compromise. With the right tools, you’ll be able to be confident when you say that nobody ever breached your most critical data.
If you have any questions or concerns about protecting your organization from information security threats or misinformation, don’t hesitate to contact the experts at Barracuda. With Barracuda’s AI-powered cybersecurity platform and solutions that are easy to buy, deploy and use, Barracuda can protect your data from a variety of complex threats and help you get out in front of misinformation. Schedule a demo and discover how Barracuda can help you strengthen your security posture and stay ahead of evolving cyberthreats

O Relatório de Invasão de Segurança de E-mail de 2025
Principais conclusões sobre a experiência e o impacto das violações de segurança de e-mail em organizações em todo o mundo
Subscreva o Blogue Barracuda.
Inscreva-se para receber destaques sobre ameaças, comentários do setor e muito mais.

Relatório de Insights do Cliente MSP 2025
Uma visão global sobre o que as organizações precisam e desejam dos seus provedores de serviços geridos de cibersegurança





