
URL manipulation techniques: Punycode, typosquatting, and more
URL manipulation techniques emerged and gained prominence in the early to mid-2000s as a method of deceiving and scamming computer users. As internet adoption grew and most users started to trust email as their preferred communication channel, cyberattacks started to emerge as well. Attackers began to look for ways to exploit email communication by manipulating URLs to deceive users and trick them into visiting malicious websites. URL manipulation-based email attacks have continued to remain a strong email attack mechanism.
The cyberthreat landscape is ever evolving. New email attacks continue to emerge, while existing attack techniques continue to evolve and target both savvy and unsavvy computer users. In one of our past blog posts, we looked at three novel phishing attack techniques — Google Translate links, use of special characters, and image attachment attacks.
This blog post focuses on similar techniques that manipulate URLs within the email body to deceive recipients and compromise their security.
What is a Punycode attack?
A Punycode attack is one such example where attackers use visually deceptive URLs to scam or phish their users. An example of a Punycode attack is seen below:
Legitimate domain: apple.com
Punycode domain: аррӏе.com
In this case, the Latin character “a” is replaced by the Cyrillic letter "а" (U+0430). This type of attack is very similar to a special character attack (where zero-width Unicode characters are used). If you search for “apple.com” on your browser window (CTRL + F or CMD + F), the search phrase will only return one result. This is because while the Punycode domain looks the same, it uses a different character set.
In addition, attackers also leverage international domain names to create similar or look-alike URLs. These types of attacks have a relatively high success rate as the URLs appear legitimate and trusted. This attack technique is also called an IDN homograph attack. Another example of this attack is G00GLE.com (similar to GOOGLE.com). Quite simple, but still very relevant today.
Since the emergence of internationalized domain names (IDNs) and the ability for attackers to easily register them, many browsers have attempted to provide protection against Punycode attacks. However, this type of attack still remains prevalent today, mainly because not every browser has adopted the same standard to deal with IDNs, and secondly, because there are legitimate use cases where special characters are used within IDNs. Both Chrome and Firefox, for example, have adapted policies to determine whether to show Unicode or Punycode for individual domains.
More details on Google’s policy on IDNs can be found here: https://chromium.googlesource.com/chromium/src/+/main/docs/idn.md
Although most modern browsers now provide this type of protection, scammers continue to leverage Punycode attacks to exploit end users by combining this technique with other attack types. For example, we have recently seen many examples of Punycode attacks being combined with “Google Translate” based attacks that we shared here.
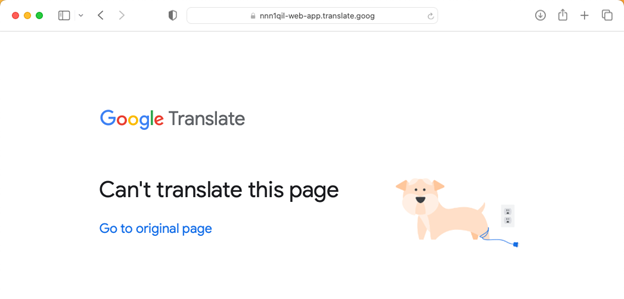
In the example above, without the translation service, the domain using Punycode would have been blocked by Google Chrome; however, while Google fails to translate the underlying website, it provides link to the “original page,” which is a malicious website that leverages Punycode in its domain name.
Typosquatting to exploit human error
Another example of a URL-based phishing attack is typosquatting, where attackers are depending on human error to phish or scam them. In this technique, an attacker will register a domain name that closely resembles a legitimate domain. Let’s look at the following example:
Legitimate domain: apple.com
Typosquatting domain: aple.com
This attack technique is different from Punycode because it doesn’t depend on using non-Latin character sets. Another example would be goglle.com instead of google.com.
Typosquatting domains are often seen used in the HREF tag of the email source code, where the actual URL text will display the more legitimate URL. This is another technique used to deceive users.
With the emergence of generative AI, it is much easier for scammers to generate a list of look-alike domains. There are multiple techniques that are leveraged by scammers when crafting typosquatting attacks. This includes using algorithms to add or strip a dash (- or _), adding or stripping characters, adding a TLD (top-level domain) before a tld, or using the wrong tld, replacing vowels, etc.
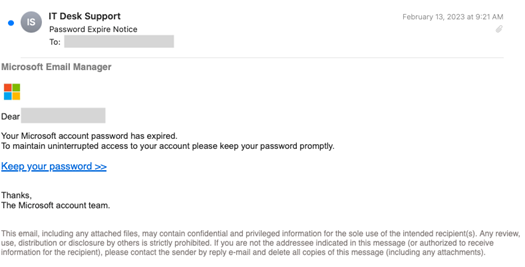
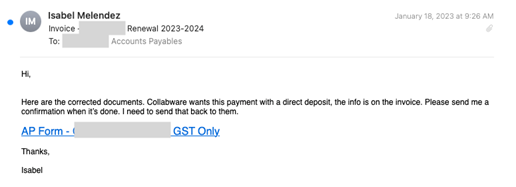
In another example, scammers targeted an accounting firm in Canada by registering a lookalike domain that included just one extra character in the domain name. The attack was carefully crafted and pointed to a website to harvest credentials.
Other URL manipulation techniques that pose a threat
In conjunction with these and previously covered phishing techniques, attackers often also use URL shorteners and watering hole attacks. URL shorteners can be used to wrap a malicious URL using a third-party URL shortening service to make it look more legitimate. Often, attackers will wrap a URL several times in order to avoid detection.
Likewise, a watering hole technique is often used to target an organization or a group of users who are known to visit a specific website often. In this case, an attacker will compromise a website using a known vulnerability and utilize links from this website to perform credential harvesting or install malware on a user’s device.
Barracuda Email Protection includes a link protection capability to ensure users do not click on any malicious URLs. LinkProtect wraps every link in an email that passes through its gateway product, and an analysis is performed at time of click of every URL to identify if the link is good or bad. While Barracuda Email Protection provides multiple security layers that include analyzing domains before email delivery and using machine learning and various stats models to identify if an email is likely good or bad, the LinkProtect capacity is critical because it acts as the last line of defense in case the payload behind a URL has changed after email delivery to point it to a malicious location. On average, LinkProtect processes roughly over 10 million requests every week, with 1% of the links found to be malicious at the time of click.
These are just some additional examples of URL-based attacks, and they have evolved and become more sophisticated over time. Some of these techniques were covered in more depth in a recent Barracuda webinar where we also looked at some real-life examples of such attacks.
As our company CTO Fleming Shi often says, “It is crucial for companies to ensure their employees are well-trained in spotting phishing attempts.” While email security solutions are necessary, every organization must ensure proper training of its employees to ensure its cyber well-being.

O Relatório de Perspetivas sobre Ransomware 2025
Principais conclusões sobre a experiência e o impacto do ransomware nas organizações em todo o mundo
Subscreva o Blogue Barracuda.
Inscreva-se para receber destaques sobre ameaças, comentários do setor e muito mais.

Segurança de Vulnerabilidades Geridas: Remediação mais rápida, menos riscos, conformidade mais fácil
Veja como pode ser fácil encontrar as vulnerabilidades que os cibercriminosos querem explorar





